Pi-hole® - Network-wide Ad Blocking
Basically Pi-hole® is an application that performs the function of being a DNS server and DHCP server if you wish for all the devices on your network. In the process it also aims to block network queries to domains in the categories of analytics, telemetry, advertisements and tracking.
The idea of trying it out had plagued me for a while, with Jeff Atwood, Scott Hanselman and Troy Hunt covering the basic setup on a Raspberry Pi.
But with a router that only serves two devices, my laptop and phone. I can't exactly call my home network sophisticated. So plan B was to use the office network, because the best testers are the ones that don't opt-in.
Although you can use a Raspberry Pi Zero, I felt safer having an actual ethernet port so I went ahead with a Raspberry Pi 3 Model B+ and 16GB microSD card for storage.



Following this great tutorial guide, my Pi-hole was up and running in under an hour.
I used the Raspbian Buster with desktop image without an issue. With the goal being a #BetterInternet I naturally chose Cloudflare as my upstream DNS provider,
1.1.1.1 is the fastest DNS resolver.
If you prefer a GUI like me, you probably prefer TeamViewer for remote access.
Here's a simply guide for setting it up on a Raspberry Pi.
If you can't set the DNS server on your router, then you set the Pi-hole to be your DHCP server to solve this. If you're not using Pi-hole as your DHCP server, you'll see IP addresses in the client column of your query log. If you are using Pi-hole as your DHCP server, you'll see the hostname of the device.
By default your Pi-hole will have the following blocklists.
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
https://mirror1.malwaredomains.com/files/justdomains
http://sysctl.org/cameleon/hosts
https://zeustracker.abuse.ch/blocklist.php?download=domainblocklist
https://s3.amazonaws.com/lists.disconnect.me/simple_tracking.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
https://hosts-file.net/ad_servers.txt
I've added the following extra lists.
https://raw.githubusercontent.com/hoshsadiq/adblock-nocoin-list/master/hosts.txt
https://raw.githubusercontent.com/notracking/hosts-blocklists/master/hostnames.txt
https://raw.githubusercontent.com/notracking/hosts-blocklists/master/domains.txt
https://www.malwaredomainlist.com/hostslist/hosts.txt
https://someonewhocares.org/hosts/zero/hosts
https://pgl.yoyo.org/adservers/serverlist.php?hostformat=hosts&mimetype=plaintext&useip=0.0.0.0
https://raw.githubusercontent.com/mitchellkrogza/Badd-Boyz-Hosts/master/hosts
https://zerodot1.gitlab.io/CoinBlockerLists/hosts_browser
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/UncheckyAds/hosts
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.2o7Net/hosts
https://raw.githubusercontent.com/azet12/KADhosts/master/KADhosts.txt
https://raw.githubusercontent.com/AdAway/adaway.github.io/master/hosts.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.Risk/hosts
https://raw.githubusercontent.com/uBlockOrigin/uAssets/master/filters/filters.txt
https://raw.githubusercontent.com/anudeepND/blacklist/master/adservers.txt
There are active communities on Reddit and Discourse. You can also find blocklists on GitHub.
After the Pi-hole is active, you'll notice websites load much faster because of the reduced bloat.
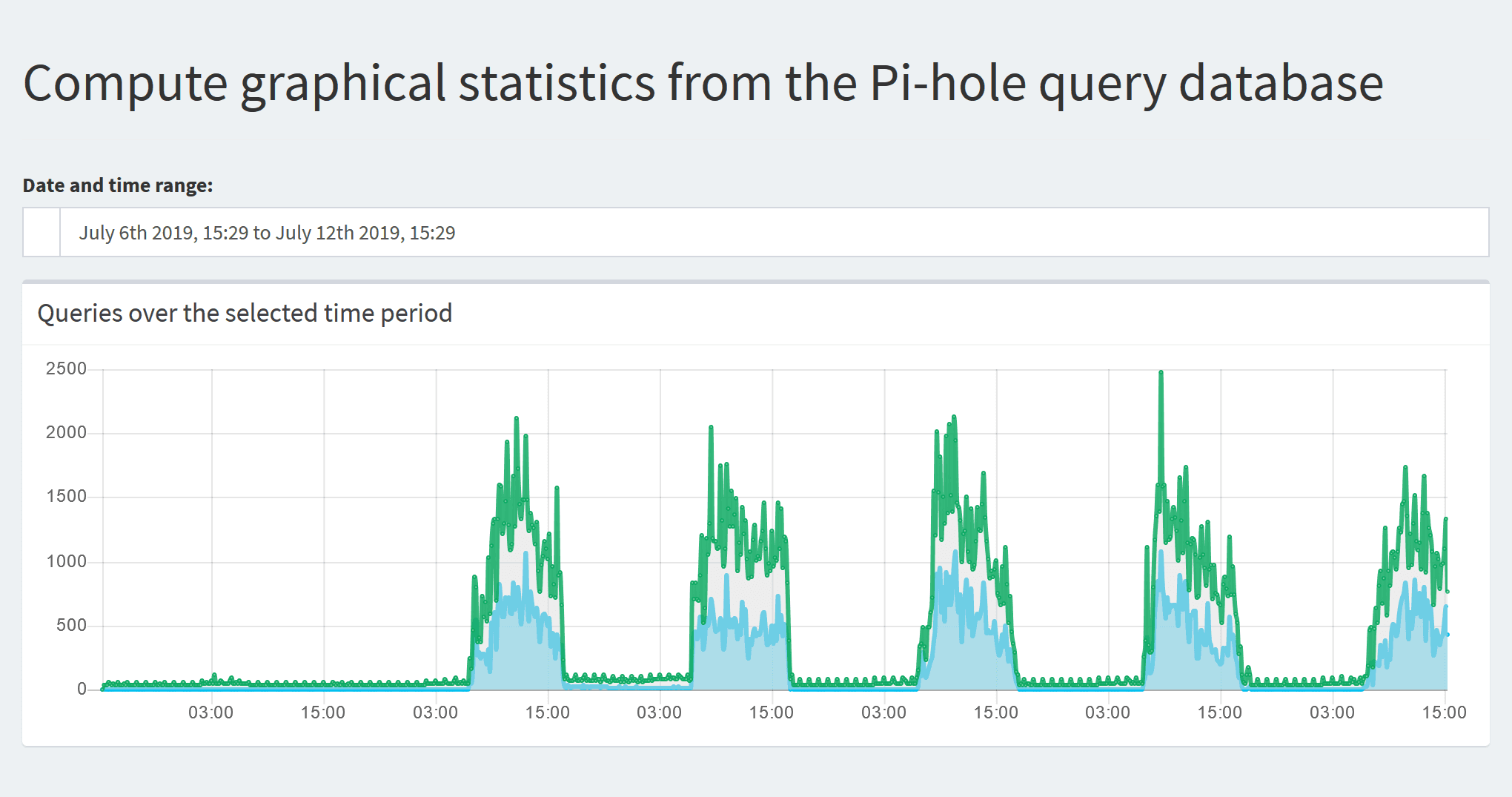
After some time you'll get a sense of the amount of queries going on in your network and the percentage being blocked. Smartphones tend to be the worst offenders with analytics integrated into apps that track every event.
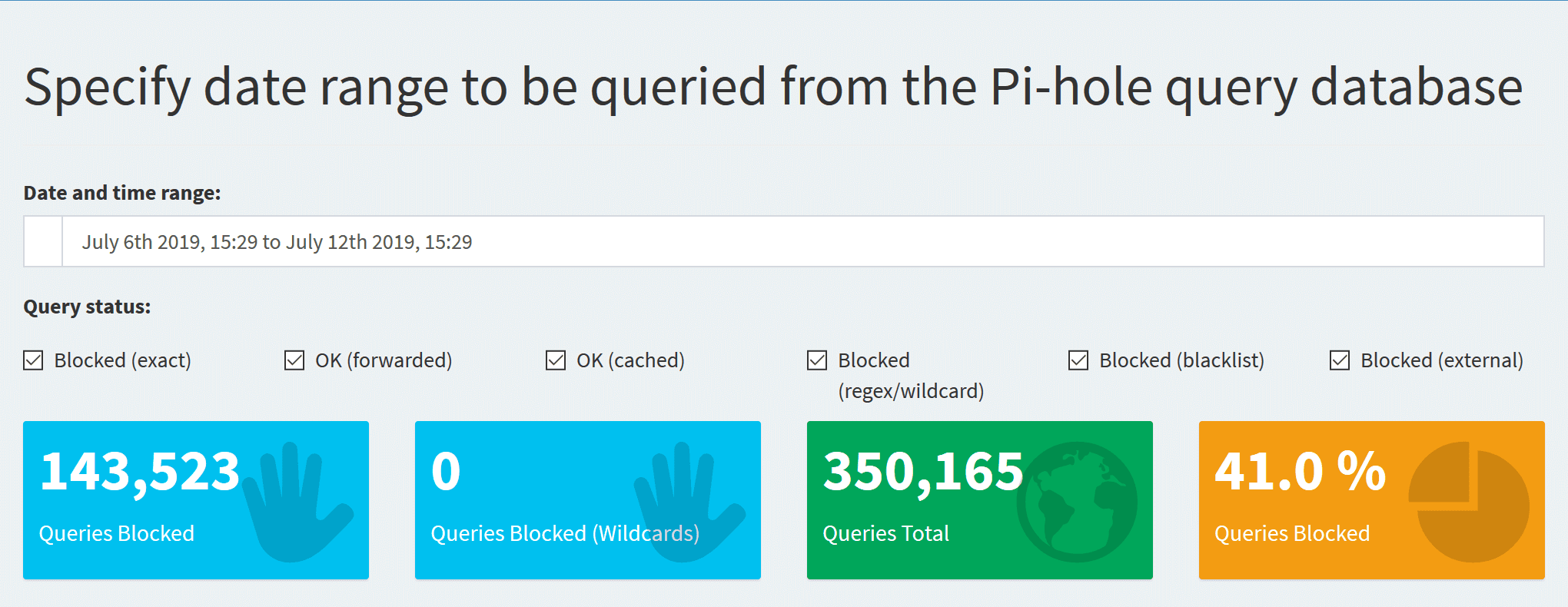
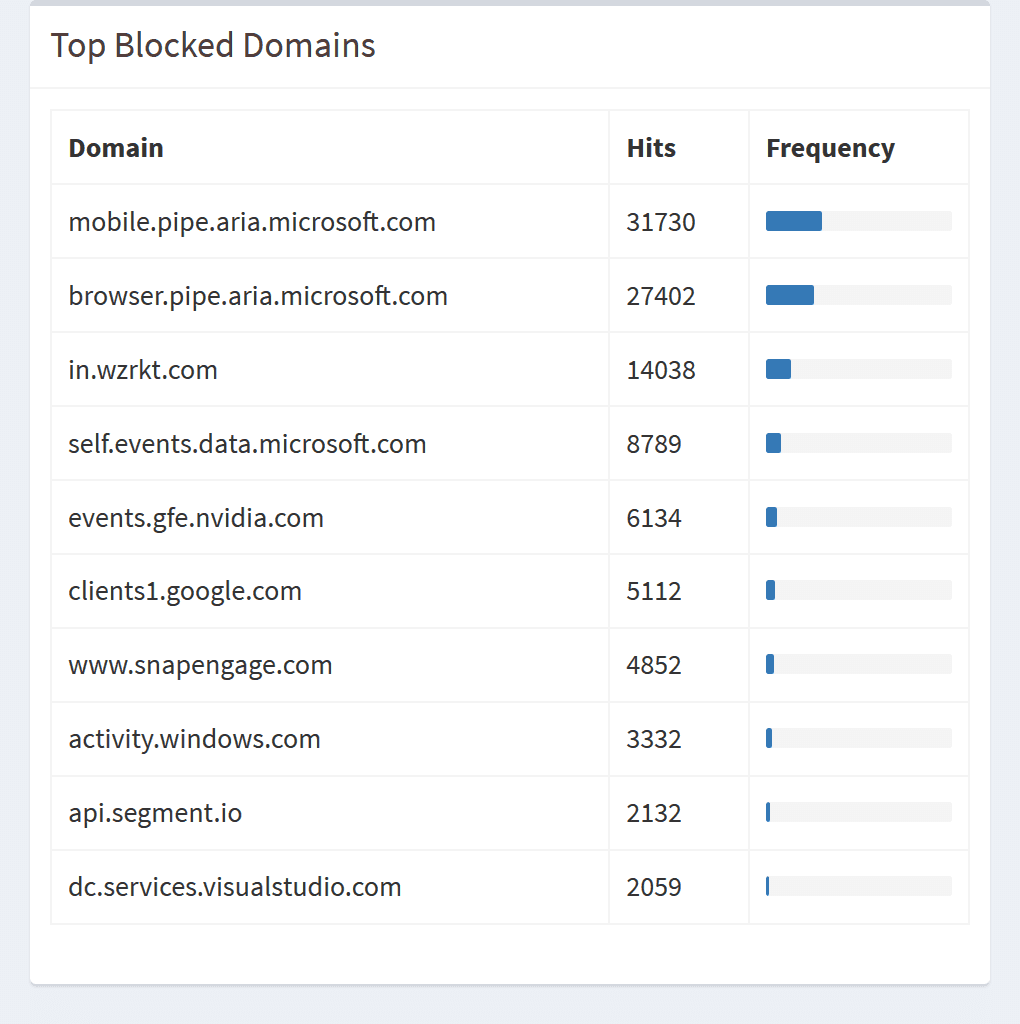
You can also tweak things, it's super simply to whitelist and blacklist domains. Although the Pi-hole will cover most of your bases, for things like YouTube's video ads you'll need to rely on uBlock Origin.
This has been a fun worthwhile project but due to its low resource usage, just using a Raspberry Pi for running Pi-hole makes it very expensive so I recommend finding another secondary project like a YouTube content cache using Squid.