Authentication can have multiple factors, commonly referred to as Multi-Factor Authentication (MFA), the common factors are:
- Knowledge: Something you know - password
- Possession: Something you have - security token generator (device)
- Inherence: Something you are - fingerprint (biometric)
Two-step verification (2SV) is an approach of having a secondary step in confirming who you are, when the secondary method is one of the other factors then it is two-factor authentication (2FA). A code you receive via SMS isn't technically 2FA.
After that brief intro, 2FA still has some weak points like phishing. I won't be breaking down FIDO U2F, I'll skip to the evolved FIDO2 standard.
Fast IDentity Online is set of open and scalable standards for strong authentication developed by the FIDO alliance whose members include Microsoft and Yubico.
I'm not a fan of traveling but I have the privilege of having friends that do so I get my hands on tech that isn't easily available in South Africa. One of these endeavours lead to me, getting my hands on a Yubico Security Key.

With the release of Windows 10 version 1903, Windows Hello got FIDO2 certification. This means I can use FIDO2 based passwordless sign in with my Microsoft Account. Even better it's in public preview for Azure Active Directory.
Below is an example of using Windows Hello to sign in passwordless to a Microsoft Account.
To set this up, go to https://account.microsoft.com/security/
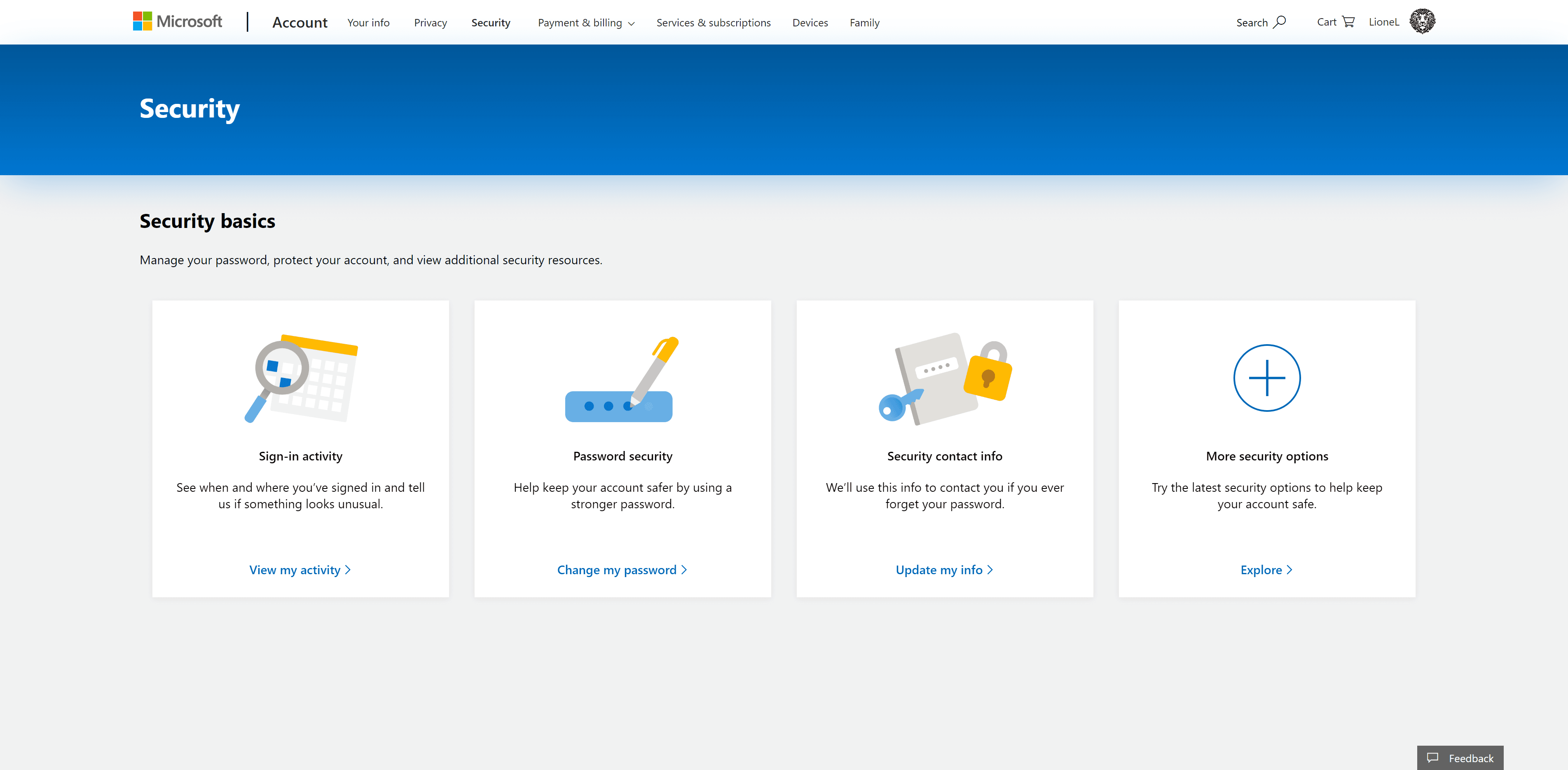
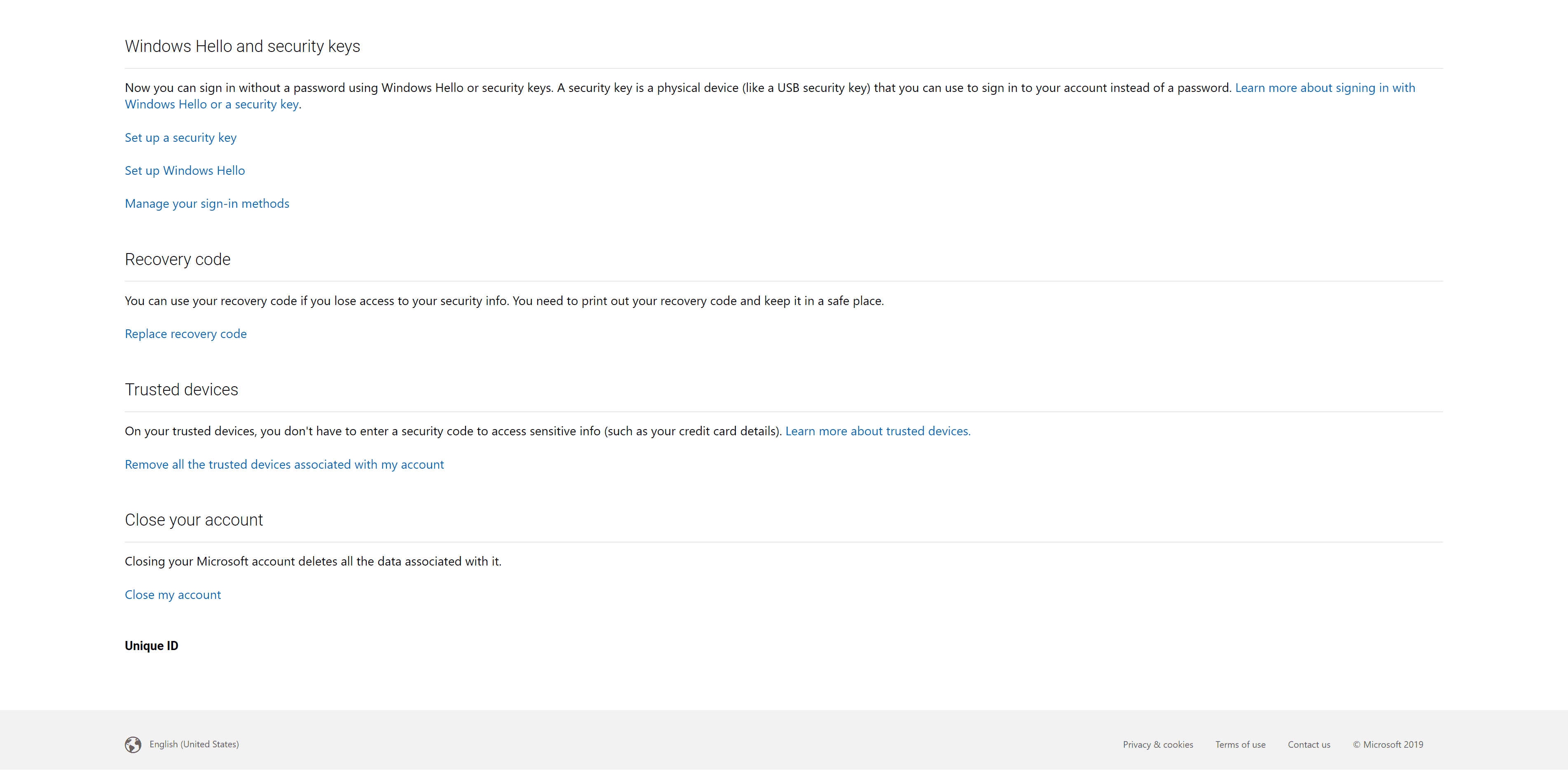
Click More security options and scroll to Windows Hello and security keys
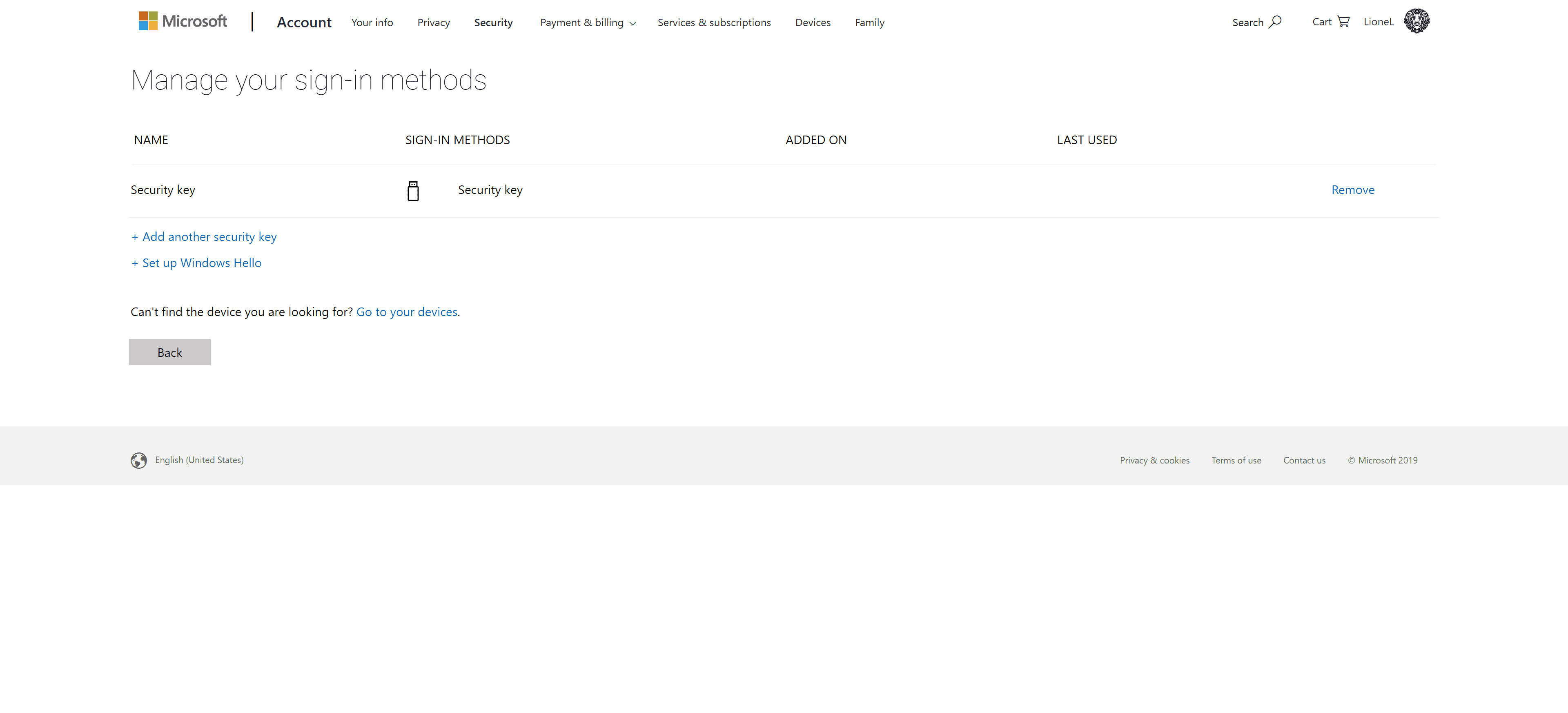
You can manage your sign-in methods at https://account.live.com/proofs/fido/manage
Below is an example of using a security key to sign in passwordless to an Azure AD Account.
To set this up, go to https://portal.azure.com/
Browse to Azure Active Directory, click on the User Settings blade then click on Manage user feature preview settings
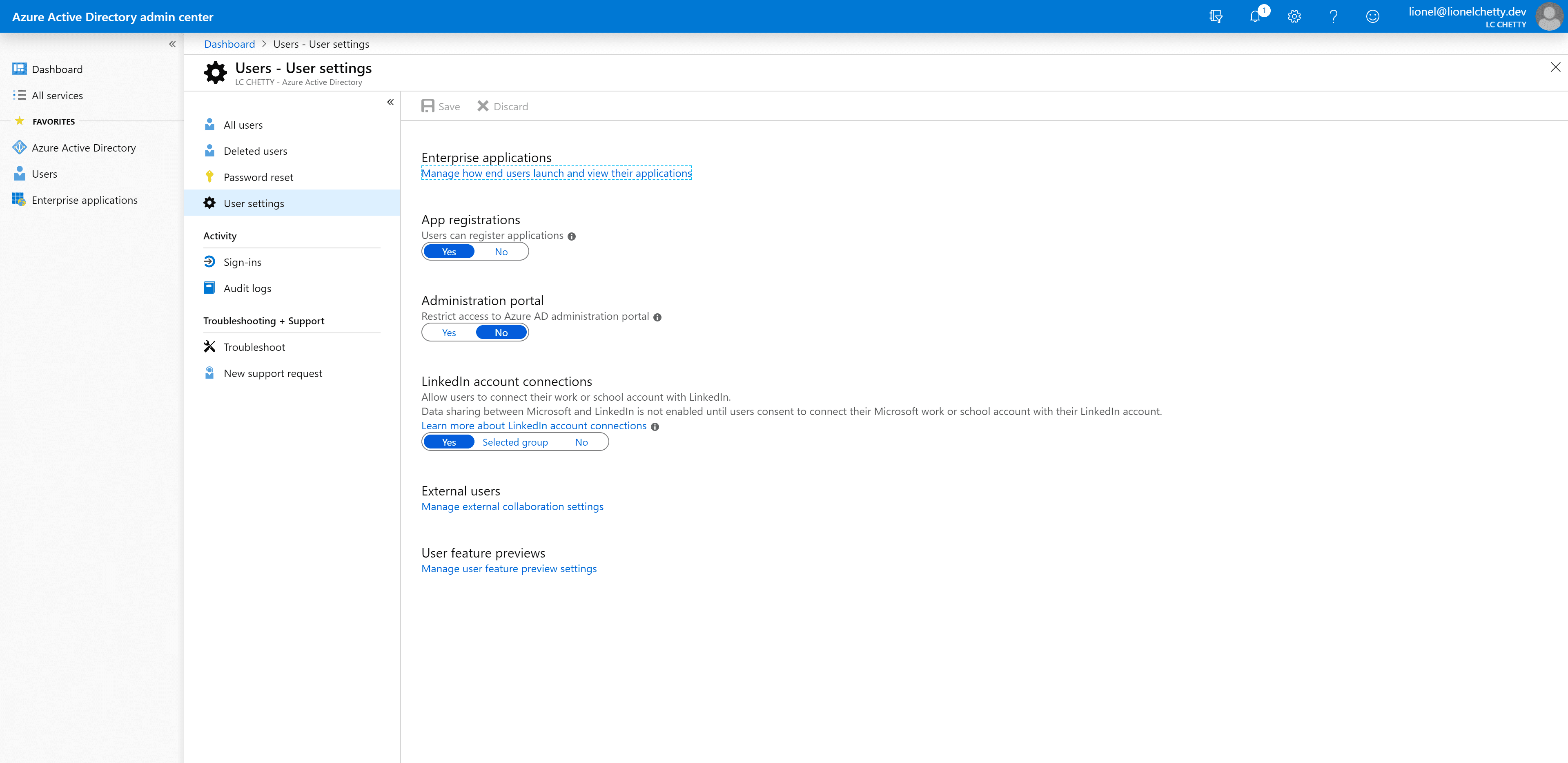
Choose selected users or all users in your directory and save.
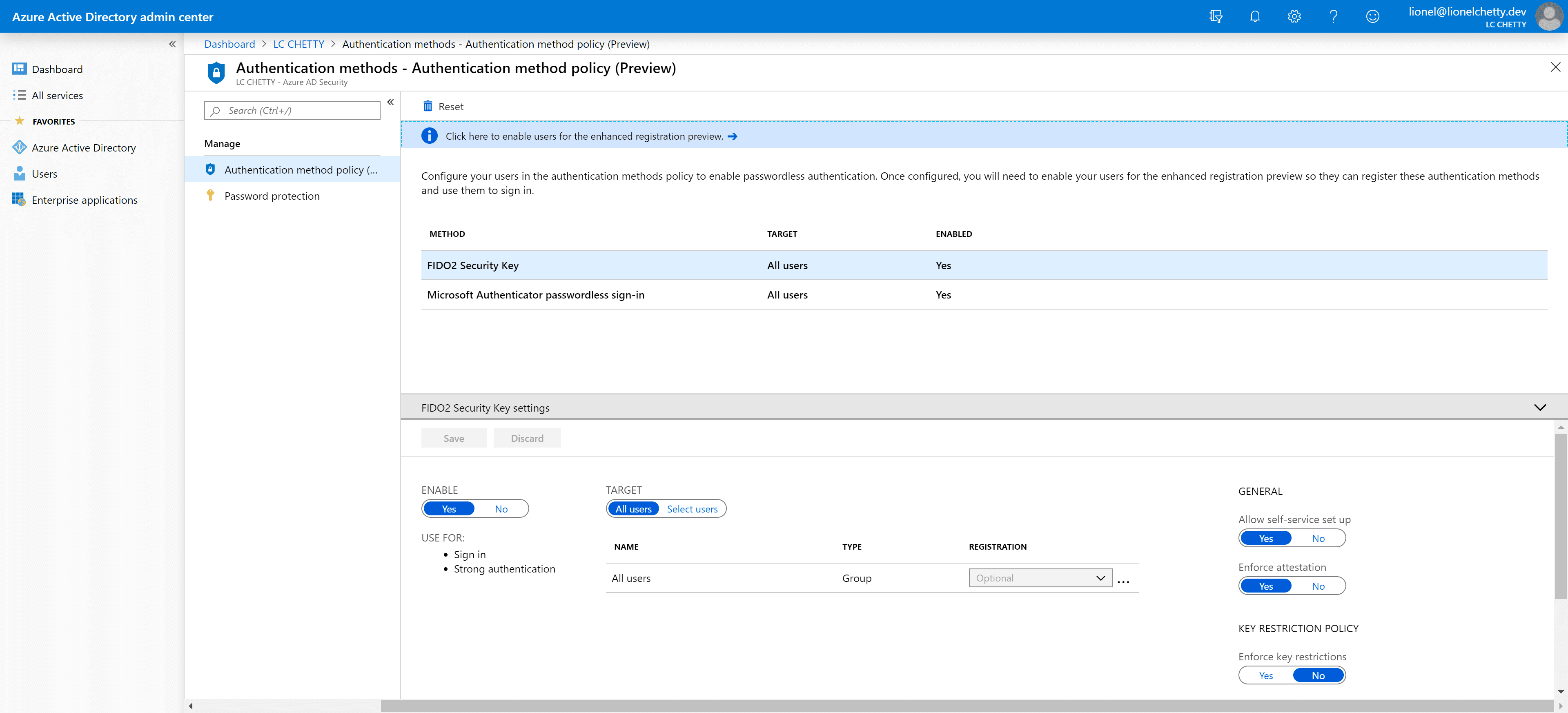
Then browse to the Authentication methods blade, select the method either FIDO2 security key or Microsoft Authenticator passwordless sign-in, then choose select users or all and save.
Then head to https://myprofile.microsoft.com
Click Security Info and register your FIDO2 security key.
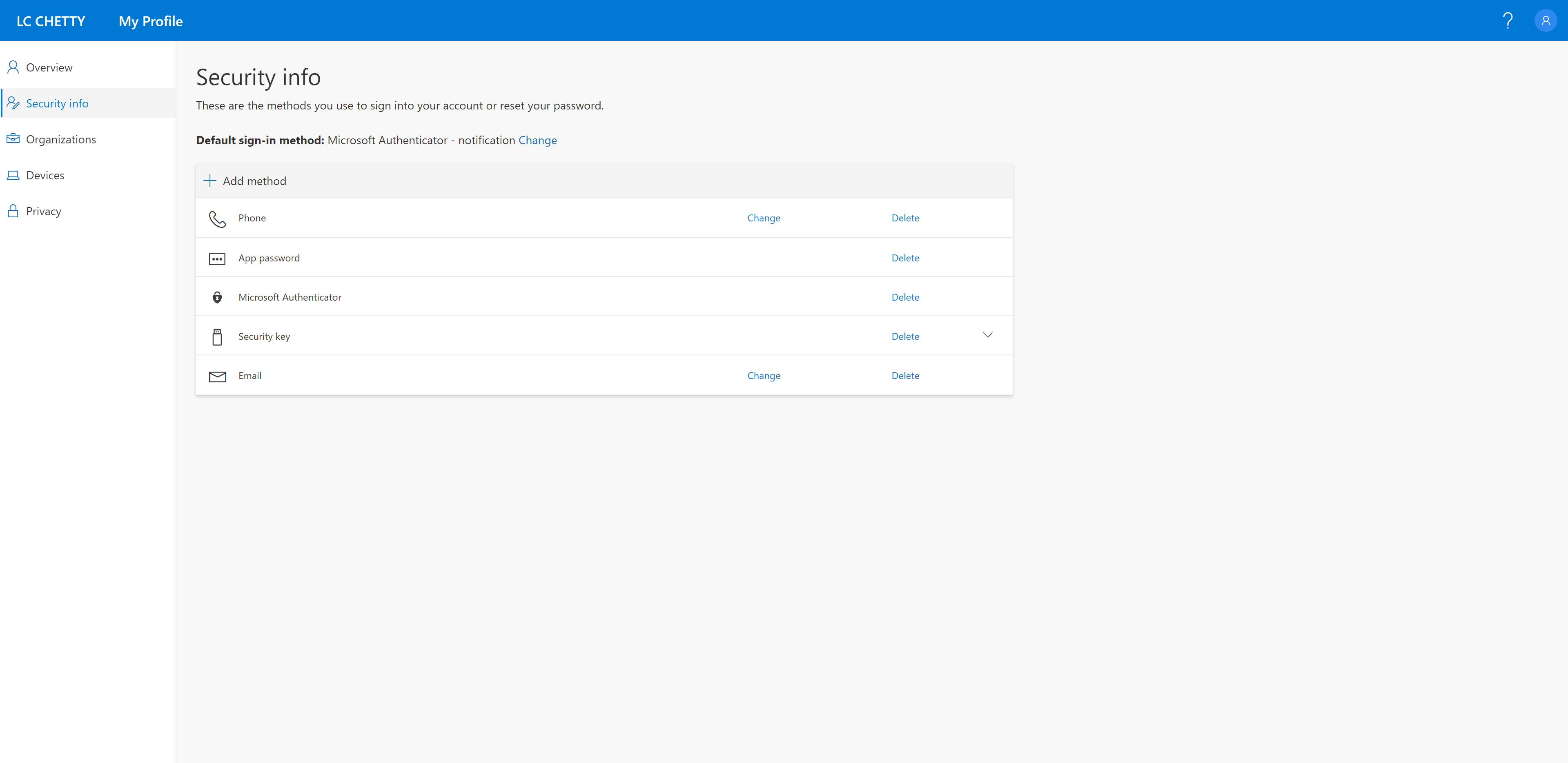
Note although you can use the Microsoft Authenticator app with many organisations, you can only enable the passwordless sign-in option with only one organisation to which your device is registered with.
With security keys you don't have any limitations. If you happen to lose it, nobody will know what services your key is associated with or be able to use it without the pin.
I haven't gone down the route of enabling security keys for Windows sign-in because I use Windows Hello, but if your devices are Azure AD joined with Windows 10 version 1809, you can easily set it up via Intune.
Overall using my fingerprint to sign-in feels more intuitive and seamless, using a security key feels more natural as you would a normal key in real life. Passwordless is easily a buzzword I can get behind and support.
